Authentication
The access to the In-app inbox should have user-scoped authorization. This means that the messages from your user's inbox shouldn't be read by another user.
Default non-secure mode
By default, the In-App Inbox APIs and libraries don't have any authentication. This is to help you get started quickly. All you need is the Engagespot API Key and your user's unique identifier (such as their email id or a UUID).
But this is dangerous for production use. Any user in your app can guess the unique identifier of another user and thus read their messages.
Secure mode
Secure mode is a feature that allows you to authenticate your in-app inbox component using a user-scoped JWT token.
Every app must enable secure mode for production usage to prevent unauthorised access to the In-App Inbox on your application.
Learn how to configure the secure mode in the next section.
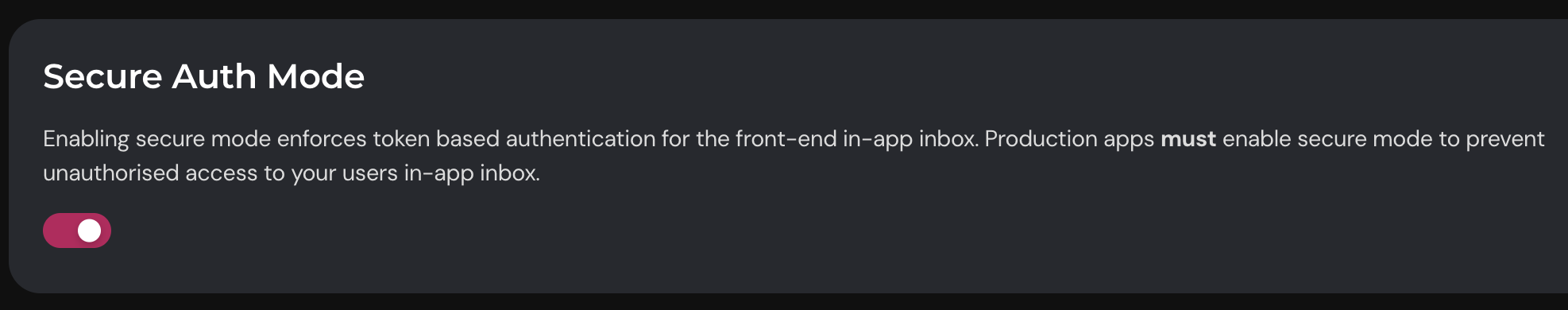
1. Enable secure mode in console.
Login to Engagespot Console -> navigate to API Credentials page and turn on Secure Auth Mode.
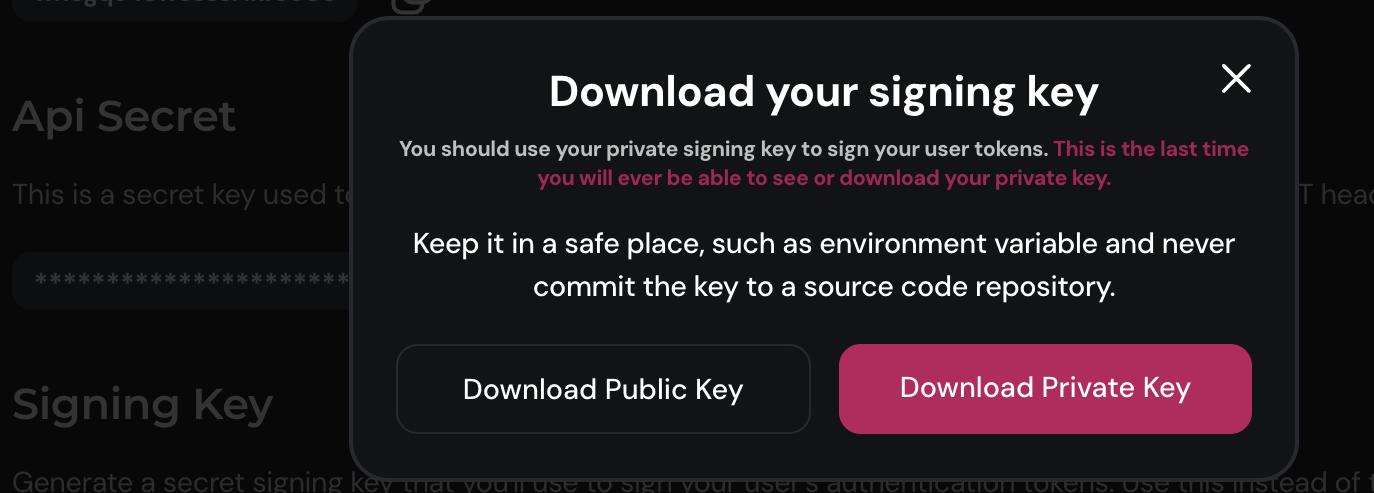
2. Generate your secret signing key
Navigate to API Credentials page and generate your public-private signing key pair and download the private key.
3. Generate the signed JWT token
You can use the functions given in our backend libraries to generate the JWT token instead of manually generating the JWT payload and signing it.
- PHP
- Node
use Engagespot\EngagespotClient;
$engagespot = new EngagespotClient( [
'apiKey' => $apiKey,
'apiSecret' => $apiSecret,
'signingKey' => $signingKey, //Make sure to read the signing key directly from the file
]);
// Create JWT token for user
$userIdentifier = 'your-users-unique-id';
$token = $engagespot->generateUserToken($userIdentifier);
// Use the generated token as needed
var_dump($token);
import { EngagespotClient } from '@engagespot/node';
const client = EngagespotClient({
apiKey: 'ENGAGESPOT_API_KEY',
apiSecret: 'ENGAGESPOT_API_SECRET',
signingKey: 'YOUR_ENGAGESPOT_SIGNING_KEY',
});
const token = client.generateUserToken('identifier');
Manually generating the JWT token (Advanced)
If you don't want to use our backend libraries, you can generate the JWT token manually.
Just make sure that the JWT payload contains the required fields and is exactly as shown in the example below. You should sign it using the private key you downloaded from the console. The algorithm should be RS256.
- PHP
- Node
<?php
require 'vendor/autoload.php';
use \Firebase\JWT\JWT;
// Load private key from file
$privateKey = file_get_contents('private.key');
// User identifier and API key
$userIdentifier = 'uniqueUserId123';
$apiKey = 'ENGAGESPOT_API_KEY';
// Payload data in the specified format
$payload = [
'sub' => "user:{$userIdentifier}",
'apiKey' => $apiKey,
'iat' => time(),
'exp' => time() + 3600 // Token expires in 1 hour
];
// Generate JWT token with RS256 algorithm
$token = JWT::enco
const jwt = require('jsonwebtoken');
const fs = require('fs');
// Load private key from file
const privateKey = fs.readFileSync('private.key', 'utf8');
const userIdentifier = 'your-users-unique-id';
// Payload data for the JWT
const payload = {
sub: `user:${userIdentifier}`,
apiKey: "ENGAGESPOT_API_KEY"
};
// Generate JWT token with RS256 algorithm
const token = jwt.sign(payload, privateKey, { algorithm: 'RS256' });
Token generation using plugins
If you're using a plugin such as the Bubble.io plugin, follow the corresponding instructions to generate the JWT token.